How to change permissions and owners in Linux using the command line
A Linux virtual private server (VPS) lets you add multiple users to simplify collaborative system management.
However, users who have full access can modify essential files and folders that affect system functionality. You must manage file permissions properly to prevent server security risks.
Linux systems provide the chmod command to change permissions. It lets you fine-tune user privileges to improve your VPS security.
In this tutorial, we will explain how to change permissions and owners in Linux using the command line utility. You will also learn the benefits of modifying user privileges, its best practices, and common issues.
A brief overview of changing file permissions and ownership in Linux:
| Required Knowledge | Basic Linux command line skills, understanding of file permissions |
| Privileges Required | Root access or sudo privileges for certain operations |
| Difficulty | Intermediate |
| Main Goal | Using chmod and chown commands, understanding file permissions |
Why change permissions and owners in Linux
In this section, we will explore several benefits of changing file and directory permissions and ownership in Linux.
Enhance security
Changing file ownership and permissions prevents unauthorized users from modifying files that may affect security. For example, they may make dangerous changes to the SSH keys or firewall configurations.
Allowing low-level users to access high-permission accounts’ files can also lead to security breaches. They may find the superuser or root credentials to take over the entire system.
Moreover, managing permissions helps prevent accidental file system removals that can compromise your server functionality.
Control access
Limiting permissions lets you fine-tune file access control in Linux. In addition to preventing mismanagement, it helps simplify auditing as you can quickly track user activities and determine the source of unauthorized actions.
Moreover, changing permissions and ownership in Linux helps improve isolation. Team members can only work and share specific files while keeping the others secure.
Maintain data confidentiality
In multi-user environments, managing file permissions ensures data confidentiality and privacy between accounts. Allowing all users to access others’ information can lead to a high risk of insider threats like data leaks.
Changing ownership helps limit the data exposure to non-authorized users. For instance, assign the product team as the sole owner of customer data to protect sensitive information.
Meet compliance and regulatory requirements
Changing permissions and file ownership in Linux systems lets you protect users’ personal data, especially if you run an internet service. It is crucial to adhere to various data privacy laws, like the European General Data Protection Regulation (GDPR).
Other regulations, like the Payment Card Industry Data Security Standard (PCI-DSS), also mandate user accountability. Granting specific users permissions helps you verify their responsibility in running the hosted service.
How to change Linux file permissions and ownership
This section will explain file ownership and permission levels in Linux and how to assign them using Linux commands.
Before proceeding, connect to your server using an SSH client like PuTTY or Terminal.
Pro Tip
If you encounter network issues when connecting to your VPS via SSH, use Hostinger’s Browser terminal feature. It allows you to run commands on your server when the SSH port is closed.
1. Understand file permission levels
Linux systems have three permission levels for files and directories – read, write, and execute. Here are their explanations:
- read (r) – allows users to view the content of a file or directory.
- write (w) – lets users edit a file’s content. For directories, they can create, delete, and move files within the folder.
- execute (x) – enables users to run a file as a script or program. Granting executable permissions over folders allows them to switch the working directory and access its extended information.
Linux also has three user classes to which you can assign the permissions:
- owner – an individual account possessing the file.
- group – a collection of users with the same role.
- others – all system-wide users who are neither the owner nor a group member.
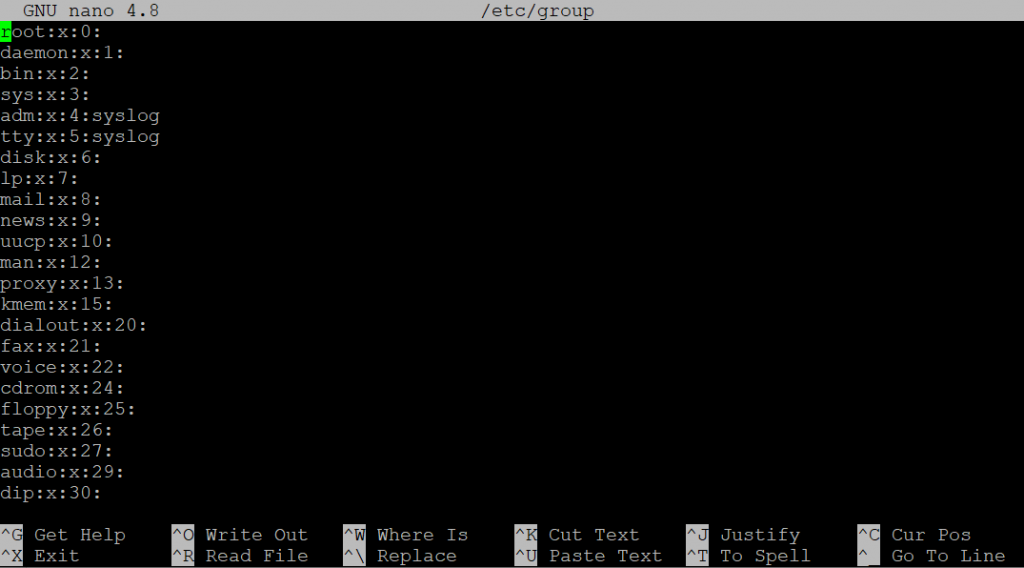
To check Linux user groups, open the group file in the /etc directory using a text editor like Nano.
Linux’s command line interface shows the Unix file permissions as a string of characters like the following example:
-rwxrwxrwx
The string starts with a file type signifier. A hyphen (–) refers to a regular file, while d represents a directory. The three-character strings are the permissions for the owner, group, and others, respectively.
If a user class doesn’t have a specific permission, a hyphen will replace the corresponding character. Consider this example:
-rwxrw-r--
The string means the owner has full permissions, while the group members can read and write the file. Since others only have r, they can read the file but not write or execute.
2. View current permissions
To check current file and subfolder permissions, navigate to the desired directory using cd. Next, run the ls command with the -l option:
ls -l
Terminal will print all the folder’s content with various information, including its permissions. Here’s an example output:
drwxrwxrwx 2 user1 admins 4096 Sep 12 04:33 config
Here’s the syntax breakdown and each column’s explanation:
- drwxrwxrwx – the folder or file’s permissions.
- 2 – the number of hard links or aliases for the file or folder.
- User1 – the owner of the file.
- admins – the group associated with the file.
- 4096 – the file or folder’s size in bytes.
- Sep 12 04:33 – the file or folder’s latest modification date.
- config – the file or folder name.
3. Change file permissions with the chmod command
To change file permissions in Linux, use the change mode or chmod command. Here’s the basic syntax:
chmod [option] [mode] [file_folder_name]
Options are parameters for modifying the command behavior. Check the chmod manual page to see the complete list. Some of the commonly used options are:
- -R – change file permissions recursively.
- -f – suppresses error messages.
- -v – displays information about the command execution.
- –help – shows the chmod manual.
The mode parameter sets the new permissions for the file or folder. Use the symbolic or octal mode – they work similarly and have the same outcome.
In addition to permissions, the chmod symbolic notation uses a single character denoting the user class and operation. Here’s the list:
| Symbol | Definition |
| u | Owner |
| g | Group |
| o | Others |
| a | All user classes (owner, group, and others) |
| + | Add permissions |
| – | Remove permissions |
| = | Set permissions to the specified values |
You can modify multiple user class permissions simultaneously by listing the modes separated using commas. Consider the following example:
chmod u+wx,g-x,o=r script.sh
The chmod command grants the script.sh file owner the write and execute permissions. It also removes the executable group permission and turns the file read-only for other users.
Pro Tip
If you omit the user when using the symbolic mode, the chmod command will set the permissions for all users.
Also known as the absolute mode, the chmod octal notation uses the following numbers to determine the user’s desired permissions:
| Number | Definition |
| 4 | Read permission |
| 2 | Write permission |
| 1 | Execute permission |
| 0 | Revoke access or no permissions |
Add the number together to set multiple permissions. For example, 3 will make the file writable and executable. Meanwhile, 7 grants the read, write, and execute permissions.
Unlike the symbolic method, the octal notation uses the numbers’ locations to determine owner, group, and others permission settings.
The following example allows the owner and group to read, write, and execute the file while revoking other users’ access:
chmod 770 script.sh
Enable the recursive mode to apply the same permissions to all files and subfolders within a directory. For example, this command grants all users write and execute permissions for the /etc/script directory contents:
chmod -R 777 /etc/script
Common use cases for the Linux chmod command include restricting access to a sensitive file that affects your system functionality. It also lets you make a script executable, resolving the bash: permission denied error.
Important! When changing folder permissions, grant the user access to parent directories.
4. Manage file ownership using the chown command
By default, an owner in Linux is a file or directory creator. If the owner belongs to a Linux group, all the other members will inherit the same permissions.
The default owner permissions differ depending on your Linux distribution. Generally, the creators can read and write their files but not execute them.
Use the chown command to change the owner of a file or folder. Here’s the syntax:
chown [new owner or group] [file or directory]
For groups, start their names with a colon (:) to allow the command to distinguish it from a user account. Carefully check the capitalization since the Linux chown command is case-sensitive. The following example sets the DevOps group as the owner of the file:
chown :DevOps deploy.sh
Changing the group ownership lets you easily manage permissions for multiple users simultaneously. Instead of granting access individually, group permissions apply to all its members.
You can also change a file’s owner and group simultaneously. To do so, add the username before the colon:
chown user:DevOps deploy.sh
Changing file or directory permissions is commonly used to enhance isolation and access control. In addition, it is useful for transferring files between users during administrative migration.
Important! Since changing a file’s ownership requires the Linux superuser privileges, use sudo when running the chown command.
Best practices for managing permissions and ownership in Linux
This section will explore best practices for Linux permissions management to help improve server administration efficiency.
Use Hostinger’s AI assistant to Write File Permission Commands
Hostinger KVM VPS hosting plans offer various features that simplify access management in Linux. For example, you can enter simple prompts into our Kodee to generate file permission commands.
This feature helps save time and effort as you can directly copy and paste the commands into your Terminal or SSH client. Moreover, it helps beginners with minimal technical knowledge to manage their servers easily.
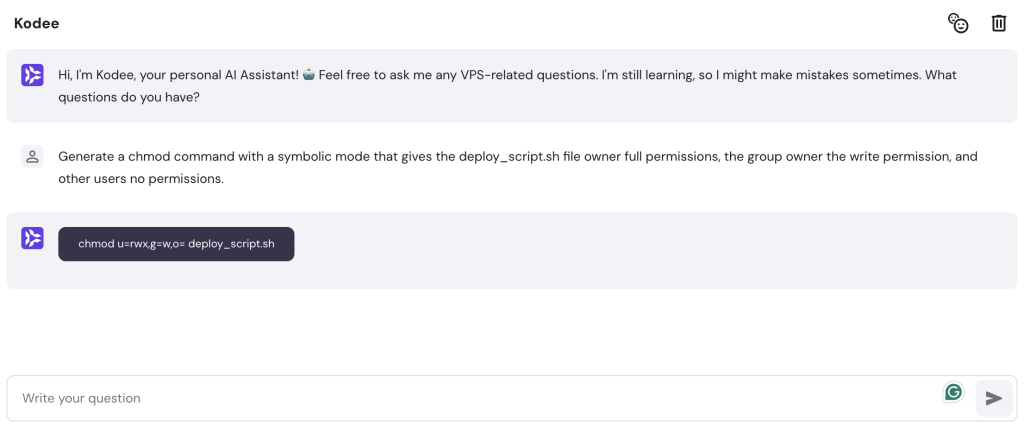
You can enter various AI prompts for VPS management to the assistant.
For example, enter: “Generate a chmod command with a symbolic mode that gives the deploy_script.sh file owner full permissions, the group owner the write permission, and other users no permissions.”

Practice the Principle of Least Privilege (PoLP)
In computer security, the PoLP principle limits user or group permissions to a minimum. It helps reduce the potential attack surface, improving server security.
Users or groups only have the necessary privileges over essential files for their roles. For example, only grant write permissions if they need to modify the file.
Do not give users excessive access to files they don’t use to prevent abuse and exploitation. Log all access permissions activity to simplify security audits in case of breaches.
Use the find command for advanced permission changes
The Linux find command lets you search for files in a directory based on specific criteria, including their permissions.
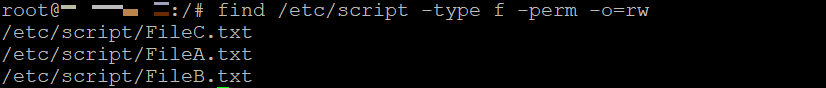
For example, run the following to find a file that the owner can read and write:
find /path/to/search -type f -perm -o=rw
The -type parameter specifies whether the command searches for files or directories. You can use either symbolic or absolute mode and specify multiple permission filters like the following:
find /path/to/search -type f -perm -u+w,g+w
find /path/to/search -type f -perm /220
The first example uses a hyphen (–) to search files with write permissions for the owner and group members. Meanwhile, we use a forward slash (/) in the second example to find a file with a write permission for either the owner or group.
To automatically change permissions and ownership, add the corresponding commands with the -exec parameter:
find /path/to/search -type f -perm -o+w -exec chmod o-w {} \;
find /path/to/search -type d -perm -u+w -exec chown newowner:newgroup {} \;
Use the first command to remove write permissions from the appropriate files. Meanwhile, the second example changes the folder’s owner with write access.
Set default permissions for new files and directories
The default file permissions in Linux are 666, while directories are 777. The umask command lets you change these settings by subtracting the default octal value with a custom number.
For example, most Linux distributions’ umask value is 022. Subtract the default value with the number. In this case, new files and directories will have the permissions 644 and 755.
You can use any unmask value. For instance, run the following command to set 554 as the default permission for a new directory:
umask 223
To check the current umask value in numeric mode, run the command without any additional parameters. Alternatively, add the -S option to output the value in symbolic notation.
Leverage Wildcard Characters for Bulk Changes
Use wildcards to change permissions and ownership of multiple files inside a folder based on their names.
Warning! Be careful when using wildcards to set different permissions. You may accidentally modify important files or folders, like the home directory.
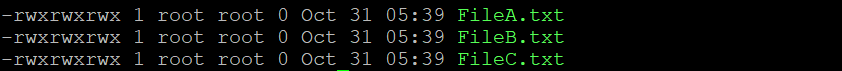
The question mark (?) wildcard represents a single character. For example, run the following to change the permissions of FileA.txt and FileB.txt in your current directory:
chmod 555 File?.txt
Use an asterisk (*) to replace zero or multiple characters. The following command example changes the ownership of Deploy_jenkins.txt and Deploy_lavarel.txt to the DevOps group:
chmod :DevOps Deploy_*.txt
Troubleshooting permissions issues in Linux
The chown and chmod commands are useful for troubleshooting file permission issues in your system. For example, you may encounter the “Permission denied” error when running a bash script or an executable file.
It happens when your current user doesn’t have the execute permission. To resolve this issue, grant the account the necessary privilege using the sudo command.
Another common issue is inadequate permissions, which hinders productivity as users can’t access essential files and directories for their tasks. This can also lead to automation script errors since it requires execution permissions to run properly.
Instead of finding and changing the file’s permissions manually, use the find command to simplify the task. Also, leverage wildcards and recursive mode to speed up the process.
Conclusion
Setting permissions in Linux lets you fine-tune system access control to improve virtual private server (VPS) security and avoid unauthorized modification. It also helps maintain user data confidentiality to comply with regulations.
Files and directories in Linux have three permissions – read, write, and execute. There are also three user classes – the file owner, a group of users, and others, which refer to those users who are neither the owner nor part of a group.
Use the ls -l command to check file permissions and ownership in a directory. To change them, use chmod and write the new rules in a symbolic or numeric mode. Meanwhile, run the chown utility as a superuser to switch the file ownership to another account or group.
Combine the find command with chown and chmod to help troubleshoot your system’s permission issues, like incorrect privileges or access denied errors. To improve efficiency, leverage Kodee to generate the commands using simple prompts.

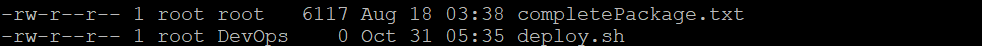
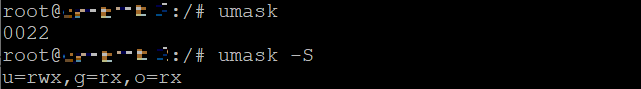

Comments
January 26 2018
Do you mind if I quote a few of your articles as long as I provide credit and sources back to your website? My blog site is in the exact same niche as yours and my users would truly benefit from some of the information you present here. Please let me know if this ok with you. Appreciate it!
February 15 2018
Sure! You're welcome to use our articles as a reference as long as your provide the necessary sources and credit! ;)
January 26 2018
Wonderful website. Lots of helpful information here. I'm sending it to some pals and additionally sharing in social media. And obviously, thank you for your effort!
January 27 2018
Excellent post. I was checking this blog and I'm impressed! Very useful info specially the last part :) I care for such information a lot. I was looking for this particular info for a long time. Thank you and best of luck.
February 15 2018
Awesome! I'm glad to hear that you found our tutorial useful! :)
July 23 2021
The operation is not permitted because its owned by root what should I do?
September 17 2021
Hi Ethan, please make sure you're connected as root user - it looks like you might not have the appropriate rights with the current user.
April 09 2023
Hi Domantas/Team, I see there was small typo/mistake under the "Using Options with chmod and chown Commands" title. it should be either "chown -R user /etc/myfiles" or "chmod -R 755 /etc/myfiles" but that has combination of both "chown -R 755 /etc/myfiles". Please take a look and change it.
April 14 2023
Hello! Thank you for noticing. I've updated the article.